Since its creation in 2010, AVCheck has been widely used by cybercriminals. This online service allowed developers to test whether their malware was detected by antivirus software. Attackers could thus refine their code until it evaded virus detection software. To scan malware while it was being developed, hackers simply had to drag their malicious files onto a platform.
After a lengthy investigation, law enforcement understood that the site played a major role in cyberattacks based on extortion. AvCheck was notably used in ransomware attacks that occurred on American soil. Hackers used the scanner to develop viruses capable of infecting a computer undetected. The malware could then be used to deploy the ransomware on the infected machine. This encrypted or stole data, giving cybercriminals leverage.
The Fall of AVCheck and 2 Other Criminal Tools
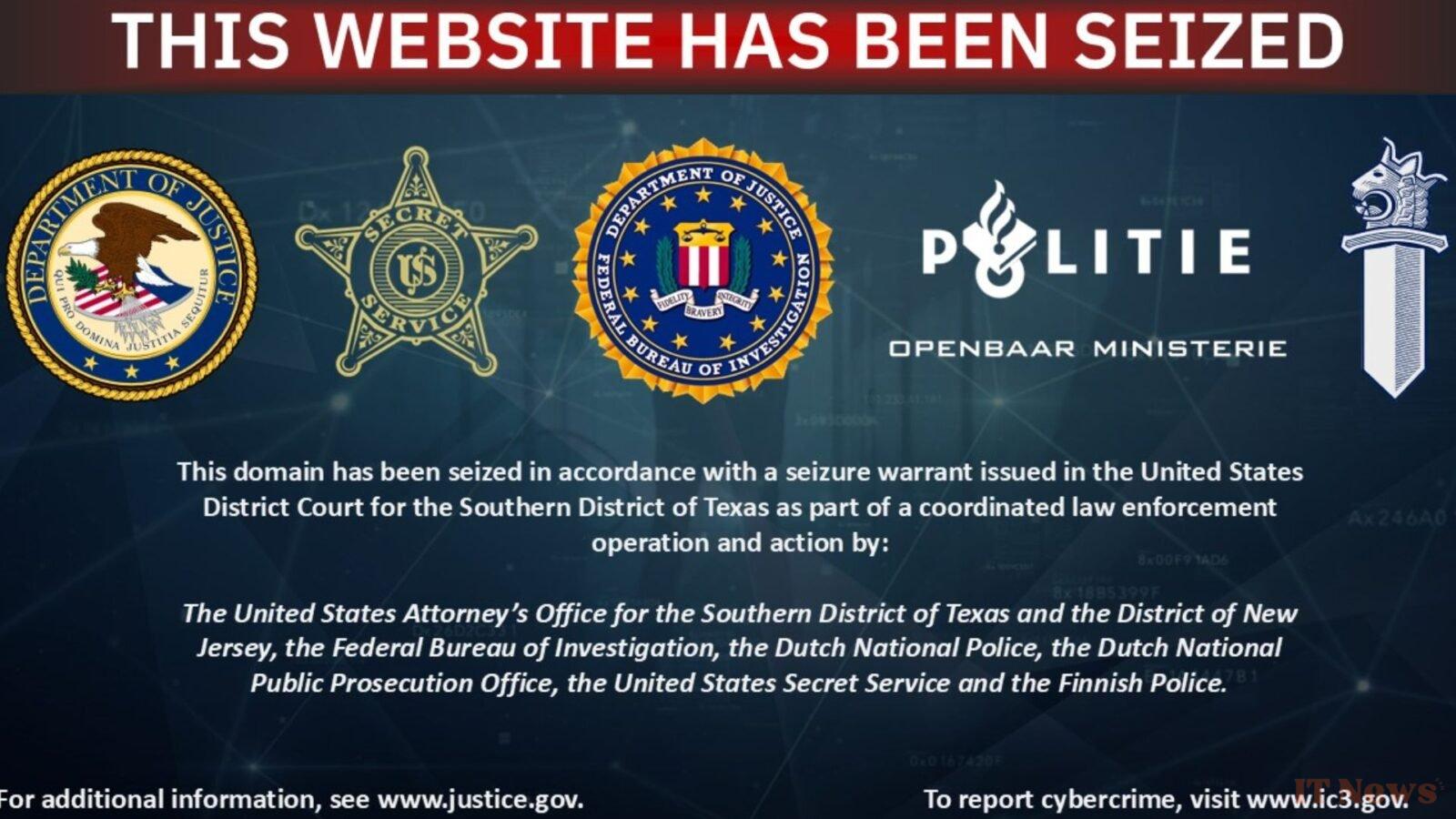
After more than fifteen years, authorities finally decided to shut down AVCheck. On May 27, 2025, law enforcement agencies in the United States, the Netherlands, and Finland seized the tool's website. It now displays a seizure notice with the logo of the authorities involved in the operation. To seize the site, the police took advantage of numerous errors made by the administrators.
The "administrators did not provide the security they promised", the Dutch police explained in a press release. According to Matthijs Jaspers, the Dutch police team leader in charge of the investigation, "taking the AVCheck service offline marks an important step in the fight against organized cybercrime." Authorities seized four domains and one server as part of the international operation. Authorities subsequently discovered that the administrators of AVCheck were linked to other services operated by cybercriminals, Cryptor.biz and Cryptor.guru. These two tools allowed cybercriminals to disguise their malware to make it undetectable by obfuscating the code or encrypting the programs. Once the code was hidden, the cybercriminals used AVCheck to test the effectiveness of their camouflage. If the software went undetected during these tests, it was then used in cyberattacks.
A fake login page to trap hackers
Before the seizure of the AVCheck website, investigators set up a fake login page. All users who attempted to log in to their accounts received a warning reminding them that the tool violates the law. The Dutch police added that law enforcement "seized the user database." Investigators have a wealth of information on the hackers who used AVCheck, including usernames, email addresses, payment information, and other "key evidence". It is therefore possible that the authorities will trace them back to them as part of their investigations.
The seizure of AVCheck stems from Operation Endgame, Operation Engame, initiated by Europol last May and described as "the largest operation ever carried out" against the malware industry. This long-term, international strike, which involved police from numerous countries and several tech giants, brought down a range of viruses, including Bumblebee, Lactrodectus, Qakbot, DanaBot, Trickbot, Warmcookie, and Danabot. By targeting the software and tools used in virus development, law enforcement is seeking to disrupt the ransomware industry. Deprived of their infection tools, hackers will have to find other ways to spread their extortion-oriented viruses.
Source: Politie.nl


0 Comments