Modern chips, like those from Apple, use a technique of "speculative execution" that allows them to go faster by "guessing" the user's upcoming requests. However, sometimes these divining gifts fall short. In this case, the chip quickly corrects its errors, but it is a process that leaves traces in the memory. Hackers can exploit these clues to retrieve sensitive information.
Speculative execution of Apple chips at fault
The hijacking of speculative execution and the resulting flaws will remind anyone who lived through the Meltdown and Spectre vulnerabilities, which in 2018 hit all x86 (Intel and AMD) and ARM (Apple) processors.
As for the vulnerabilities we are dealing with today, they were discovered by researchers at the Georgia Institute of Technology and the Ruhr University in Bochum. For a hacker, exploiting them is very simple: all it takes is a malicious web page.
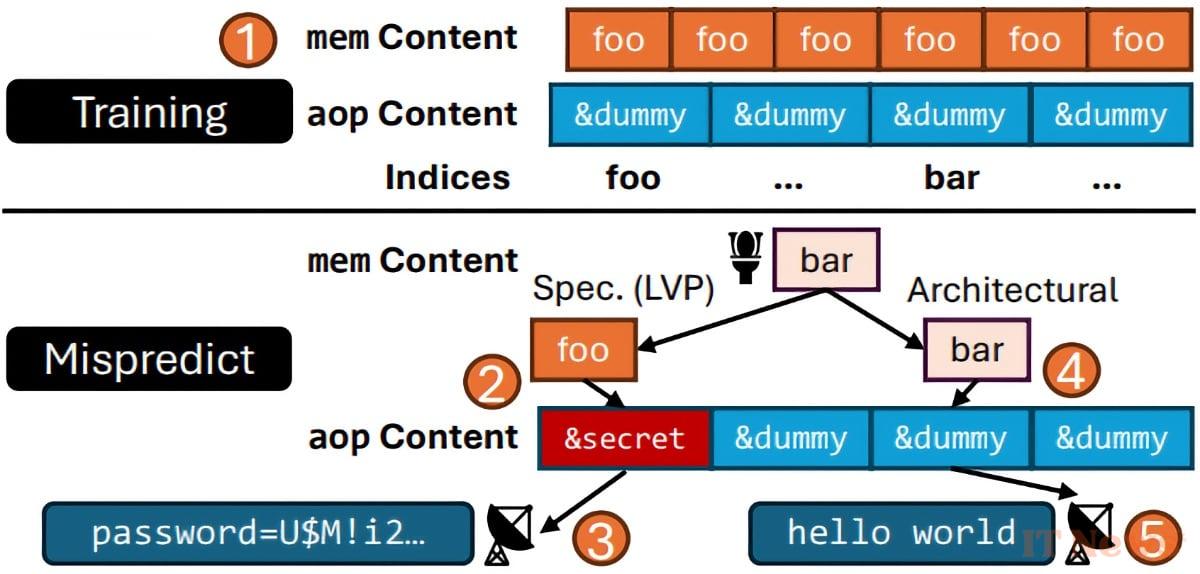
The first problem, called False Load Output Prediction, or simply FLOP, is a bad prediction of data values. It has been discovered in recent Apple chips: M3 and M4, which equip the Mac and the iPad Pro, as well as the A17 Pro, under the hood of the iPhone 15 Pro, 15 Pro Max, and the iPad mini 7th generation. When properly exploited, this flaw can be used to retrieve private data from Safari, such as the sender and subject of an email in Proton Mail, Google Maps history, or iCloud calendar events.
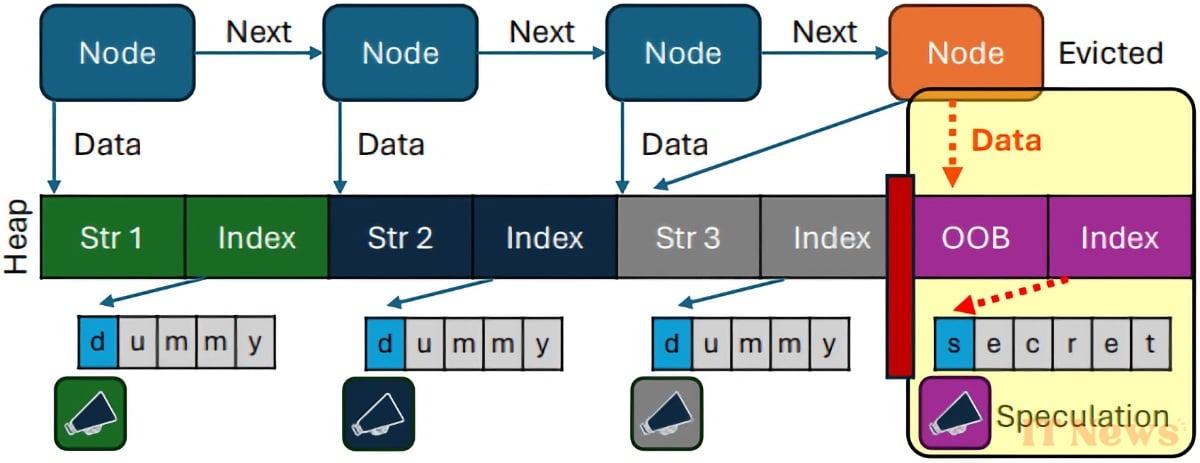
The second issue, called Speculative Load Address Prediction (SLAP), is a poor prediction of memory locations. It affects the M2, M3, M4 chips, as well as the A15, A16, and A17 Pro. An attacker can take advantage of this to siphon off data such as the content of Gmail emails, Amazon purchase history, or Reddit activity.
FLOP and SLAP are two different ways for attackers to exploit the prediction errors of Apple processors. The manufacturer was notified of SLAP in March 2024, and of FLOP in September of the same year, without them having been corrected. However, the execution method is very simple: hackers do not need direct physical access to the machines, nor to know the login credentials, nor even to inject malware. A simple malicious web page containing specific scripts (JavaScript or WebAssembly) is sufficient.
Apple thanks the researchers and has acknowledged the existence of these vulnerabilities. It assures that "based on our analyses, we do not believe that these flaws pose an immediate risk to our users". However, the manufacturer is planning patches. In the meantime, the best recommendation is to disable JavaScript execution in Safari (Settings > Security) and Chrome (Settings >Privacy & Security > Site Settings > Javascript), which may render many sites unusable.
Source: BleepingComputer



0 Comments