A phishing campaign is underway. The emails sent are recognized as coming from Google, but the aim is to steal your personal information. The utmost caution is advised.
Unfortunately, we receive phishing emails very often. In most cases, our email detection systems are powerful enough to automatically redirect them to the Spam folder. Aside from forcing us to empty it from time to time, these scam messages ultimately have very little impact. Hackers know this very well, so they are doubling their ingenuity to slip through the net and encourage you to consider their scams as legitimate.
Read also – Beware, this phishing campaign uses Google Calendar to try to trap you
And one of the best ways to do this is to impersonate a real entity: your bank, your electricity or internet provider, a company you have already dealt with… But these messages also generally do not pass the barrier of protections. At most, a person will think that the latter made a mistake by sending the email to spam. Hackers have done much better: they managed to impersonate Google 100%, even using their real sending address.
Beware of this Google email, it's a clever phishing attempt
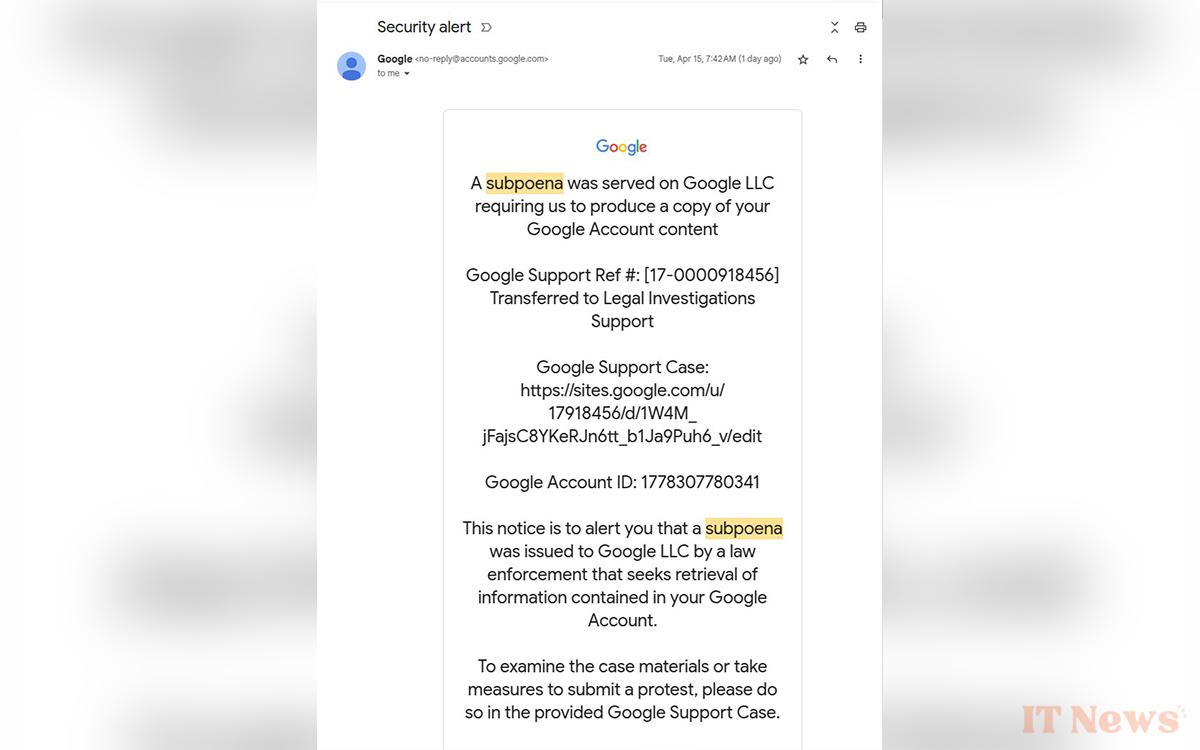
Developer Nick Johnson is raising the alarm on X (Twitter). He received an email saying that Google had received a court order to provide data concerning his account. Surprise: the message was sent from the address [emailprotected], the one used by the company, and the message is even integrated into other very real security alerts. The company's anti-spam systems did not respond.
A link redirects to a website created with the Google Sites tool, a way to accentuate the deception. Buttons to “view the file” or “send additional documents” then redirect to pages where you must enter your personal information. This information will, of course, be retrieved by hackers who can use it as they see fit. So, they should definitely not do this if you receive this message.
How did the hackers manage to impersonate Google?
It must be admitted that this phishing attempt is a feat. According to Nick Johnson's analysis, two flaws were used here. The first concerns Google Sites, which was used to create the fake pages that you land on from the email. The second is the one that allowed the message to be authenticated as coming from Google.
First, the hackers registered a domain name and associated it with a Google account opened for the occasion. Next, they created a Google OAuth app using the entire contents of the fraudulent email as the name for the app. OAuth is a protocol for authorizing the application to use another website's secure API on behalf of a user. A "delegation of authorization" in short.
Read also – The Google Drive scam flooding email boxes can trap you, here's how to avoid it
By allowing the previously created Google account to access this OAuth app, the scammers obtained the sending of a security notification email signed by Google. All they had to do was forward this email to the victims, which resulted in the one you see in the screenshot above. Clever. The developer shared his findings with the company, but they ended the discussion by responding that this was the normal behavior of their system. After posting on X, she finally announced that she would fix the flaws raised.
Recently I was targeted by an extremely sophisticated phishing attack, and I want to highlight it here. It exploits a vulnerability in Google's infrastructure, and given their refusal to fix it, we're likely to see it a lot more. Here's the email I got: pic.twitter.com/tScmxj3um6
— nick.eth (@nicksdjohnson) April 16, 2025


0 Comments