The security of our passwords often comes down to little things. An extra number, a capital letter, a special character... or not. However, according to the latest report from the American cybersecurity company Hive Systems, the power of consumer graphics cards has reached such a level that it renders most "classic" passwords obsolete. The 2025 report uses a configuration of twelve RTX 5090s—the fastest graphics card currently available—to simulate what a motivated hacker could accomplish.
Ever more powerful GPUs, ever weaker passwords
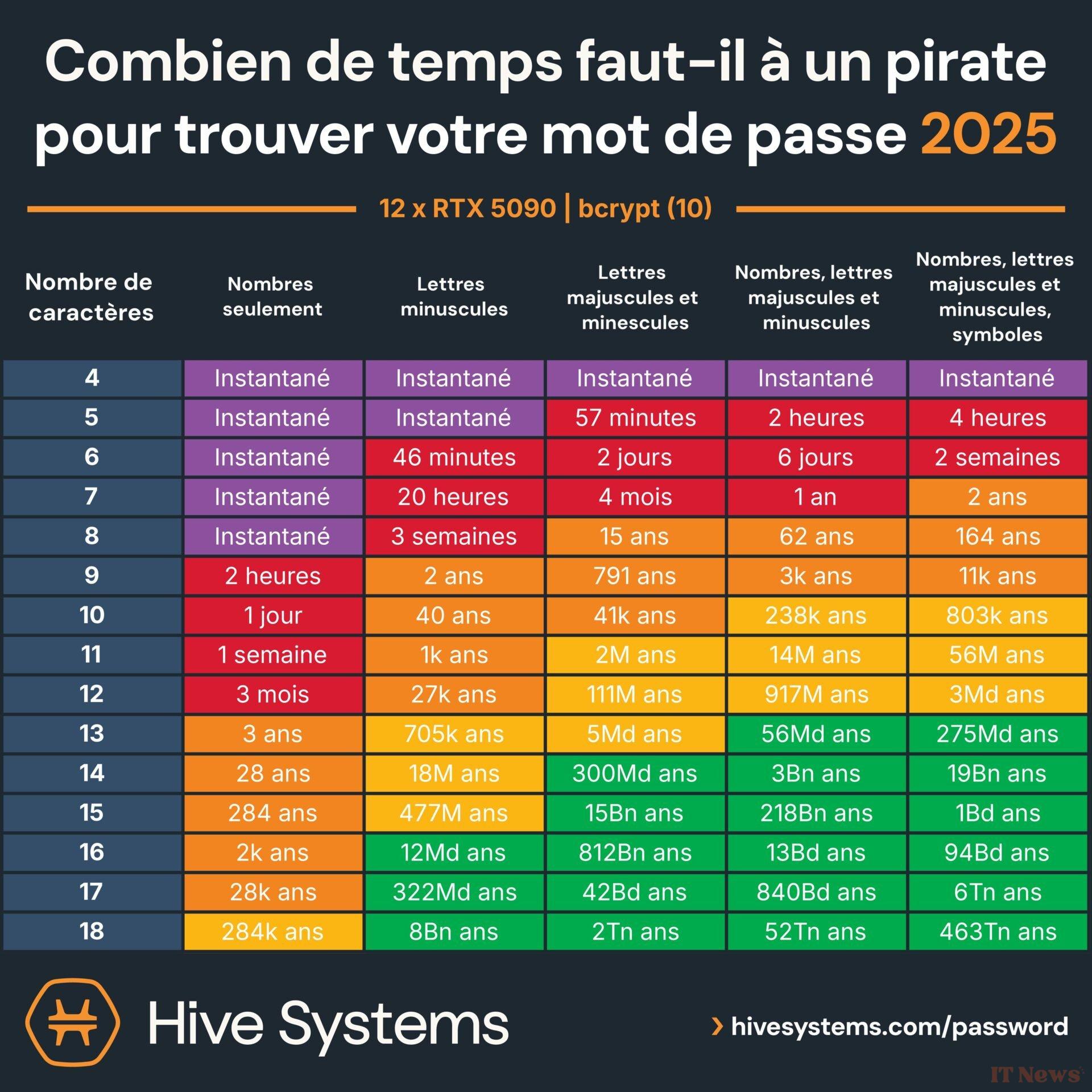
The result? An eight-digit password can be cracked instantly, even with a single one of these cards. A sequence of eight lowercase letters barely lasts three weeks against a single GPU. And if that password is a dictionary word or appears in a data leak? It's immediately compromised.
And that's just a glimpse. Hive Systems also tested the strength of passwords against the capabilities of computing centers used to train artificial intelligences like ChatGPT. With the A100 and H100 GPUs (Nvidia) used by OpenAI, a password of eight lowercase letters can be cracked in 30 minutes. A more complex password (lowercase, uppercase, numbers, special characters) lasts about two months... but nothing insurmountable.
What this study shows above all is the rapid obsolescence of traditional protections. If you are still using eight-character passwords, even random ones, you are in the red zone. Hive reminds us that a good defense is based on three essential pillars. First, a long and complex password, ideally generated randomly with a password manager.
Then the activation of two-factor authentication (2FA), favoring code-generating applications or, better, physical keys (like YubiKey). Finally, the use of passkeys, a new password-free authentication method, which prevents both brute force attacks and phishing attempts.
At the same time, Hive looked at concrete incidents, notably the LastPass data leak in 2022. At the time, the platform used a low number of hash iterations by default to encrypt passwords, making their decryption much faster than expected. According to some researchers, it could have taken just 2.5 years to crack some master passwords—an eternity for a human, but an opportunity for organized cybercriminal groups.
Even the best hashing algorithms (like bcrypt or PBKDF2 SHA-256) are no match for weak, predictable, or reused passwords. The rise of hardware, from consumer-grade GPUs to infrastructure used to train AIs, is changing the rules of the game.



0 Comments