American and Japanese researchers have discovered a rather worrying security flaw in a component found in a myriad of high-tech devices: MEMS microphones. We'll explain everything to you.
While a vulnerability in Microsoft 365 Copilot's AI has just been discovered, American and Japanese researchers have discovered another, equally worrying one. This time, the flaw in question concerns a component found in a myriad of high-tech consumer devices: MEMS (microelectromagnetic systems) microphones.
MEMS microphones, also known as silicon microphones, are etched on a semiconductor silicon wafer. They are found in laptops and smart assistants like Google Home.
All it takes to spy on microphones is an antenna, a radio, and some AI.
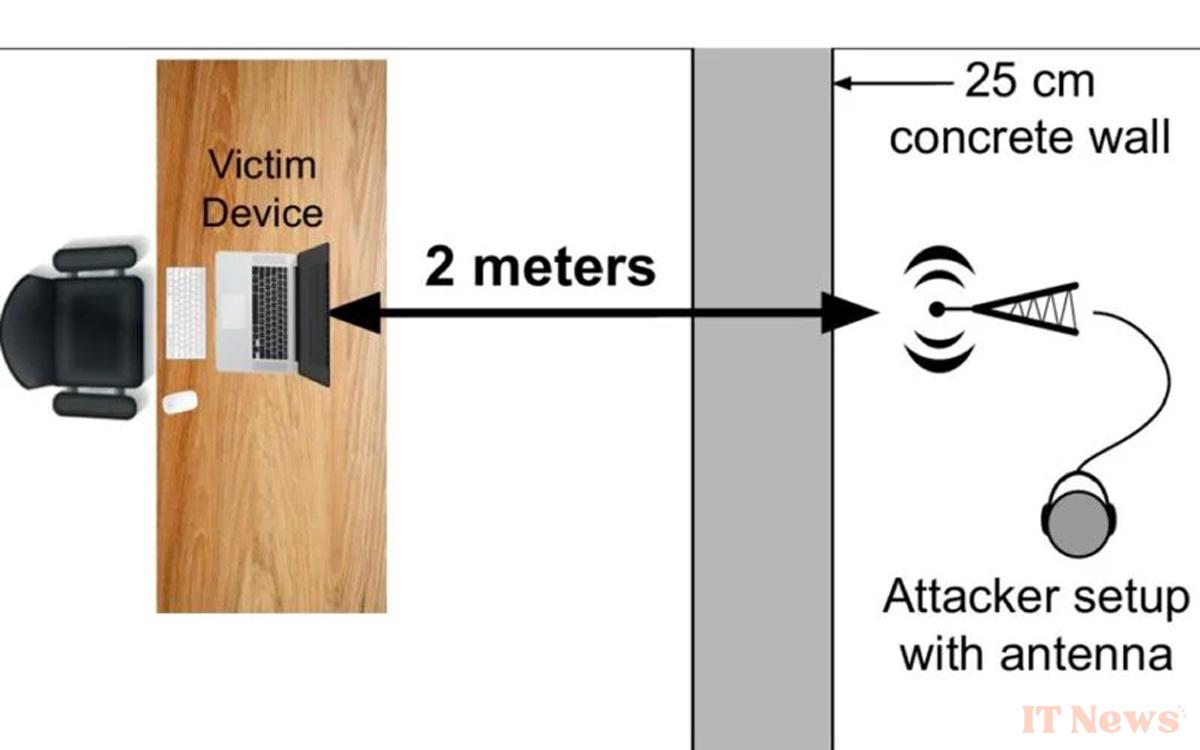
However, researchers from the University of Florida and the University of Electrocommunications in Japan have detected a new flaw in these components. Specifically, they demonstrated that even through a 25 cm concrete wall, attackers could accurately reconstruct speech using just an FM receiver, a copper antenna, and machine learning AI tools.
Indeed, each harmonic of the digital pulses used in MEMS microphones retains acoustic information, making it possible to recover the original audio information by simple FM demodulation with a standard radio receiver and a standard copper antenna. In this way, an attacker can exploit this vulnerability to remotely record everything a MEMS microphone hears without installing malware on the device.
During testing, the attack had a 94.5% success rate in recognizing spoken digits, up to 2 meters from a laptop placed behind a 25 cm concrete wall. Then, Open AI's generative AI was used to reconstruct the voice with an error rate of only 6.5%!
A vulnerability that affects many devices
As part of these tests, the researchers tested a range of laptops, Google Home smart speakers, and videoconferencing headsets. This eavesdropping actually worked wonderfully on laptops. Why? Because MEMS microphones are usually connected via long, flat, unshielded cables, which turns them into an antenna.
Of course, the researchers shared their discovery with the manufacturers concerned, including STMicroelectronics and Vesper (a Qualcomm subsidiary). To reduce the risks, they recommend reviewing the layout of MEMS microphones in laptops, for example, by reducing the length of the connectors and shielding them. “A 1% change in the audio processing clock frequency also reduces signal clarity, without affecting microphone performance,”they add.




0 Comments